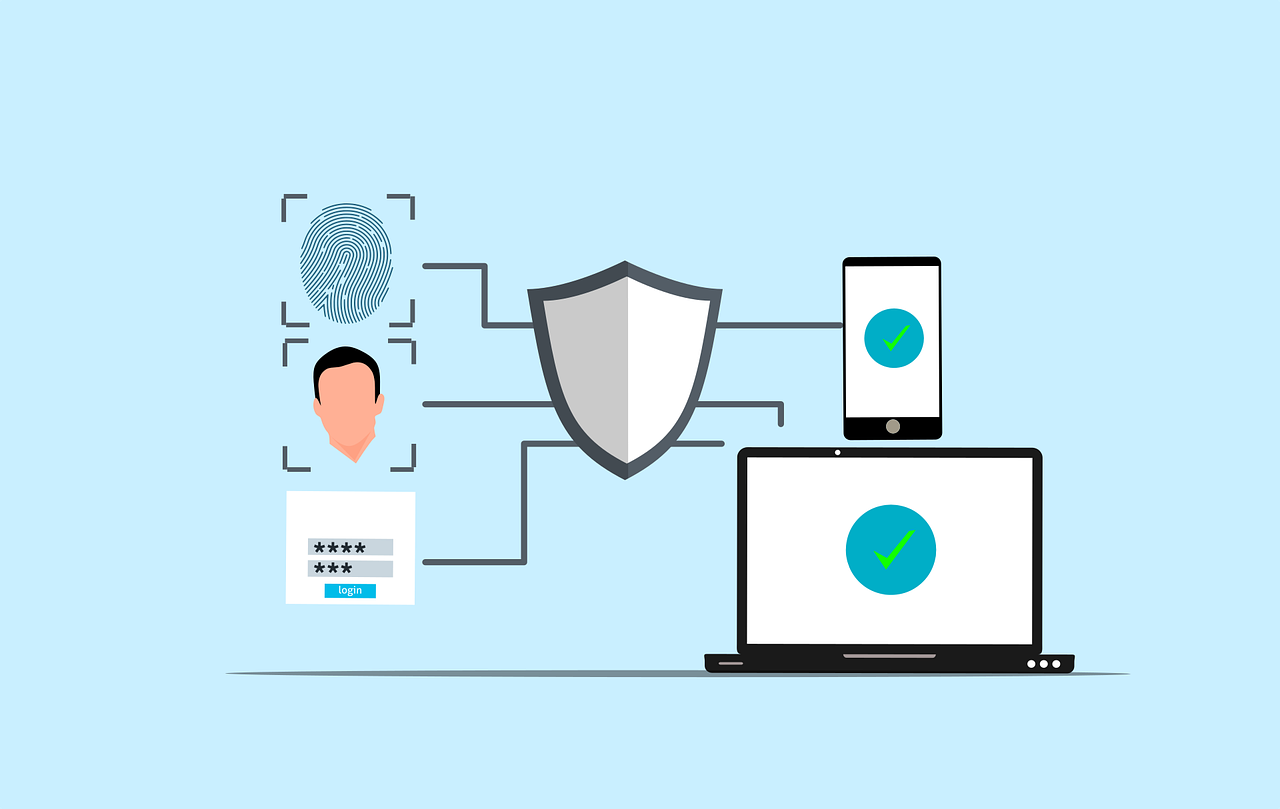
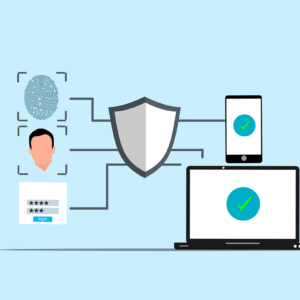
This self-learning course focuses on network security, providing participants with the knowledge and skills necessary to protect network infrastructures, data, and systems from unauthorized access, cyber threats, and vulnerabilities. Participants will explore key concepts such as encryption, firewalls, intrusion detection systems (IDS), VPNs, and network security protocols. The course covers best practices for securing both wired and wireless networks, managing risks, and implementing security policies to ensure confidentiality, integrity, and availability of information. Through interactive assessments, learners will test their knowledge and earn rewards based on their performance, such as scholarships, soft supports, and potential job opportunities for exceptional results.
Features include:
– A self-paced, interactive learning format that covers the principles and practices of network security.
– Rewards for top performers, including scholarships, soft supports, and career opportunities.
– A structured learning path that connects network security theory with practical applications in securing modern network infrastructures.
Skills Developed:
1. Understanding the Fundamentals of Network Security and the Importance of Protecting Network Infrastructure
2. Exploring Different Types of Network Threats, Including Malware, Phishing, DDoS Attacks, and Insider Threats
3. Implementing Network Security Protocols, including SSL/TLS, IPsec, and HTTPS
4. Configuring Firewalls, Routers, and Intrusion Detection/Prevention Systems (IDS/IPS) to Prevent Unauthorized Access
5. Using Virtual Private Networks (VPNs) for Secure Communication and Remote Access
6. Encrypting Data in Transit and at Rest to Protect Sensitive Information
7. Securing Wireless Networks, Including Wi-Fi Encryption and Access Control Measures
8. Monitoring and Analyzing Network Traffic to Identify Potential Security Breaches
9. Managing Network Security Policies and Implementing Access Control Mechanisms (e.g., ACLs, Role-Based Access Control)
10. Conducting Vulnerability Assessments and Penetration Testing to Identify Weaknesses and Ensure Network Resilience
Incentives and Achievements:
– Engage with assessments to test your knowledge, with rewards such as scholarships, soft supports, and job opportunities for high achievers.
– Exceptional learners may gain access to network security tools, case studies, or additional materials related to careers in cybersecurity, network administration, or IT security.
How it Works:
– Complete interactive modules focused on network security concepts, tools, and techniques.
– Participate in hands-on exercises, configuration challenges, and case studies to deepen understanding.
– Your performance will be assessed based on quizzes, assignments, and practical exercises, determining progression through the course and eligibility for rewards.
Target Audience:
This course is ideal for network administrators, IT security professionals, systems engineers, and students interested in learning how to secure network infrastructures and protect digital assets. It is well-suited for individuals pursuing careers in network security, cybersecurity, ethical hacking, or information assurance.
Start your journey into network security today and unlock opportunities for personal and professional growth in this critical and fast-evolving field!